Latest Posts
Researchers found 26 new vulnerabilities in the USB drivers used in Windows, Linux, macOS and other systems.
In our daily life, USB interface can be found everywhere, routers, printers, projectors, PC computers, desktop computers, etc., and its usage frequency is extremely high.
Of course, as the input and output interface of the hardware device, its safety is also very important.
Recently, researchers found 26 new vulnerabilities in the bulk flash drives used in Windows, Linux, macOS and other systems.
In fact, a large amount of users have accepted the fact that “USB devices are not safe”.
In our previous articles, we have repeatedly introduced USB-related security incidents, such as the BadUSB vulnerability that made billions of USB devices “sleepless”. From keyboards, printers to Usb flash drives, none is spared.
But this time, there are too many vulnerabilities and many major operating systems are compromised.
After further understanding, the research team was led by Hui Peng from Purdue University and Mathias Payer from Swiss Federal Institute of Technology Lausanne. The 26 new vulnerabilities were discovered through the new tool USBFuzz created by them. This type of tools is called “fuzzer” by team members.
It is said that the fuzzer is a gather of multiple applications that can help security researchers enter large amount of invalid, accidental or random data into other applications.
Afterwards, security researchers analyze the behavior of the tested software to discover new bugs, some of which may be used maliciously.
To test bulk flash drives, Peng and Payer jointly developed USBFuzz. It is a new fuzzer that is designed to test USB driver stack of modern operating systems.
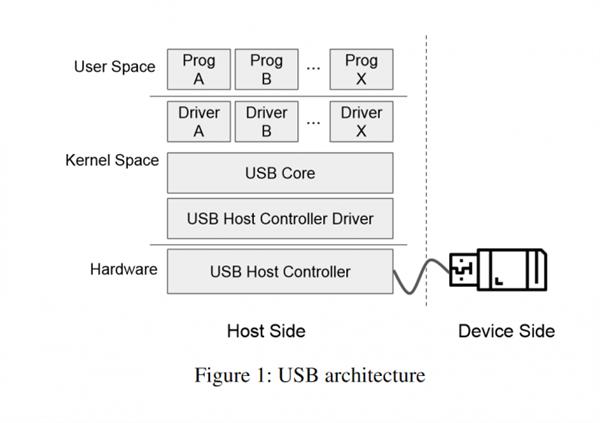
According to the researchers, The core part of USBFuzz is that it uses software-emulated USB devices to provide random device data to driver (when they perform IO operations).
In addition, the research team also stated: “Since the emulated USB device works at the device level, it is straightforward to port it to other platforms.”
This allows the research team to test USBFuzz not only on Linux, but also on other operating systems.
Researchers tester USB Fuzz on the 9 latest versions of the Linux kernel: v4.14.81, v4.15, v4.16, v4.17, v4.18.19, v4.19, v4.19, v4.19.1, v4.19.2 and v4.20 -rc2 (the latest version at the time of evaluation). It is also tested on FreeBSD 12 (the latest version), MacOS 10.15 Catalina (the latest version), and Windows (8 and 10 versions with the latest security updates).
After the test, the research team said that with the help of USBFuzz, the team found 26 new bugs in total.
Including one bug found in FreeBSD, three bugs found in MacOS (two caused unplanned restart, one caused the system to freeze), and four were found in Windows 8 and Windows 10 (causing a blue screen of computer crash).
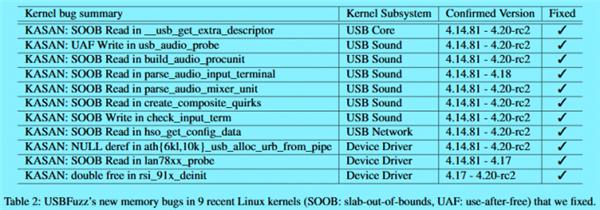
In comparison, the most serious ones were found targeting Linux systems, there were 18 bugs in total.
Among them, 16 are high-risk memory vulnerabilities that target various Linux subsystems (USB core, USB sound and net-work), and 1 targets at USB for Linux.
In response, Peng and Payer stated that they reported these bugs to the Linux kernel team and made patch recommendations to ease the “burden of kernel developers when they fix the reported vulnerabilities.”
At the same time, the research team also stated that 11 out of 18 of the Linux vulnerabilities have received patches since they were first reported last year.
Among these 11 bugs, 10 of them also received CVE, which is the only code assigned to a major security vulnerability.





Leave a comment